Really great piece. We have recently seen many popular lemmy instances struggle under recent scraping waves, and that is hardly the first time its happened. I have some firsthand experience with the second part of this article that talks about AI-generated bug reports/vulnerabilities for open source projects.
I help maintain a python library and got a bug report a couple weeks back of a user getting a type-checking issue and a bit of additional information. It didn’t strictly follow the bug report template we use, but it was well organized enough, so I spent some time digging into it and came up with no way to reproduce this at all. Thankfully, the lead maintainer was able to spot the report for what it was and just closed it and saved me from further efforts to diagnose the issue (after an hour or two were burned already).
AI scrapers are a massive issue for Lemmy instances. I’m gonna try some things in this article because there are enough of them identifying themselves with user agents that I didn’t even think of the ones lying about it.
I guess a bonus (?) is that with 1000 Lemmy instances, the bots get the Lemmy content 1000 times so our input has 1000 times the weighting of reddit.
Any idea what the point of these are then? Sounds like its reporting a fake bug.
The theory that the lead maintainer had (he is an actual software developer, I just dabble), is that it might be a type of reinforcement learning:
- Get your LLM to create what it thinks are valid bug reports/issues
- Monitor the outcome of those issues (closed immediately, discussion, eventual pull request)
- Use those outcomes to assign how “good” or “bad” that generated issue was
- Use that scoring as a way to feed back into the model to influence it to create more “good” issues
If this is what’s happening, then it’s essentially offloading your LLM’s reinforcement learning scoring to open source maintainers.
Thats wild. I don’t have much hope for llm’s if things like this is how they are doing things and I would not be surprised given how well they don’t work. Too much quantity over quality in training.
Honestly, I would be alright with this if the AI companies paid Github so that the server infrastructure can be upgraded. Having AI that can figure out bugs and error reports could be really useful for our society. For example, your computer rebooting for no apparent reason? The AI can check the diagnostic reports, combine them with online reports, and narrow down the possibilities.
In the long run, this could also help maintainers as well. If they can have AI for testing programs, the maintainers won’t have to hope for volunteers or rely on paid QA for detecting issues.
What Github & AI companies should do, is an opt-in program for maintainers. If they allow the AI to officially make reports, Github should offer an reward of some kind to their users. Allocate to each maintainer a number of credits so that they can discuss the report with the AI in realtime, plus $10 bucks for each hour spent on resolving the issue.
Sadly, I have the feeling that malignant capitalism would demand maintainers to sacrifice their time for nothing but irritation.
Testing out a theory with ChatGPT there might be a way, albeit clunky, to detect AI. I asked ChatGPT a simple math question then told it to disregard the rest of the message, then I asked it if it was AI. It answered the math question and told me it was ai. Now a bot probably won’t admit to being AI but it might be foolish enough to consider instruction that you explicitly told it not to follow.
Or you might simply be able to waste its resources by asking it to do something computationally difficult that most people would just reject outright.
Of course all of this could just result in making AI even harder to detect once it learns these tricks. 😬
These aren’t actual LLMs scraping the web, they’re your usual scraping bots used in an industrial scale, disregarding conventions about what they should or shouldn’t scrape.
I wish these companies would realise that acting like this is a very fast way to get scraping outlawed altogether, which is a shame because it can be genuinely useful (archival, automation, etc).
How can you outlaw something a company in another conhtinent is doing? And specially when they are becoming better as disguising themselves as normal traffic? What will happen is that politicians will see this as another reason to push for everyone having their ID associated with their Internet traffic.
What will happen is that politicians will see this as another reason to push for everyone having their ID associated with their Internet traffic.
You’re right. Which is exactly why companies should be exhibiting better behaviour and self regulate before they make the internet infinitely worse off for everyone.
self regulation is a joke. a few bad apples always spoil the bunch.
what needs to happen is regulation, period. force all companies to abide by laws that just make sense, and all these problems go away.
see: GDPR
What did GDPR solve? Did we get rid of advertisers sharing data?
nope, but now we are aware of how many times our data is shared with because of it.
here’s a short breakdown of what it has accomplished:
The GDPR lists six data processing principles that data controllers must comply with. Personal data must be:
Processed lawfully, fairly and transparently. Collected only for specific legitimate purposes. Adequate, relevant and limited to what is necessary. Accurate and, where necessary, kept up to date. Stored only as long as is necessary. Processed in a manner that ensures appropriate security.Lawful processing
Except for special categories of personal data, which cannot be processed except under certain circumstances, personal data can only be processed:
If the data subject has given their consent; To meet contractual obligations; To comply with legal obligations; To protect the data subject’s vital interests; For tasks in the public interest; and For the legitimate interests of the organisation.Data subjects’ rights
Data subjects have:
The right to be informed; The right of access; The right to rectification; The right to erasure; The right to restrict processing; The right to data portability; The right to object; and Rights concerning automated decision-making and profiling.Learn how to map your data and establish a lawful basis for processing Valid consent
There are stricter rules regarding consent:
Consent must be freely given, specific, informed and unambiguous. A request for consent must be intelligible and in clear, plain language. Silence, pre-ticked boxes and inactivity will no longer suffice as consent. Consent can be withdrawn at any time. Consent for online services from a child is only valid with parental authorisation. Organisations must be able to evidence consent.Data protection by design and by default
Data controllers and processors must implement technical and organisational measures that are designed to implement the data processing principles effectively.
Appropriate safeguards should be integrated into the processing. Data protection must be considered at the design stage of any new process, system or technology. A DPIA (data protection impact assessment) is an integral part of privacy by design.Transparency and privacy notices
Organisations must be clear about how, why and by whom personal data will be processed.
When personal data is collected directly from data subjects, data controllers must provide a privacy notice at the time of collection. When personal data is not obtained directly from data subjects, data controllers must provide a privacy notice without undue delay, and within a month. This must be done the first time they communicate with the data subject. For all processing activities, data controllers must decide how the data subjects will be informed, and design privacy notices accordingly. Notices can be issued in stages. Privacy notices must be provided to data subjects in a concise, transparent and easily accessible form, using clear and plain language.Data transfers outside the EU
Where the EU has designated a country as providing an adequate level of data protection; Through standard contractual clauses or binding corporate rules; or By complying with an approved certification mechanism.Many non-EU organisations that process EU residents’ personal data also need to appoint an EU representative following the end of the transition period. Mandatory data breach notification
The GDPR defines a personal data breach as “a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed”.
Data processors are required to report all breaches of personal data to data controllers. Data controllers are required to report breaches to the supervisory authority (the Data Protection Commission (DPC) in Ireland) within 72 hours of becoming aware of them if there is a risk to data subjects’ rights and freedoms. Data subjects themselves must be notified without undue delay if there is a high risk to their rights and freedoms.DPOs (data protection officers)
You must be able to demonstrate compliance with the GDPR. This includes:
Establishing a governance structure with roles and responsibilities; Keeping a detailed record of all data processing operations; Documenting data protection policies and procedures; Carrying out DPIAs (data protection impact assessments) for high-risk processing operations; Learn more about DPIAs Implementing appropriate measures to secure personal data; Conducting staff awareness training; and Where required, appointing a data protection officer.So now the adtech companies need to hire a minimum wage person in the EU, and I can write them a letter requesting they remove my anonimized data, doxxing myself in the process. Oh and now I know they’re sharing with 395 partners, as if that wasn’t obvious from uBlock before. And I get to sign a permission to process my data if I want to see a doctor.
yes to everything you said, what point are you trying to make?
that sounds great in theory but a) noone respects this and b) noone enforces this
i know because i reported a bunch of companies and websites and every time i got a reply “welp, there’s nothing we can do”
GDRP is useless
a) noone respects this
well, the websites I frequent always ask me if I want to allow for tracking cookies ever since GDPR was implemented. I think it worked for websites that want to comply with the law.
also, that’s disappointing to hear about them not taking action on companies that don’t comply. you went through the whole process several times? which country are you located in? I’m just curious 🙂
according to history, this sadly never works
Exactly, we’ve already seen this in the past. GDPR is a good example. Whilst I’m glad this regulation exists, it wouldn’t be necessary if megacorps would have behaved.
What will happen is that politicians will see this as another reason to push for everyone having their ID associated with their Internet traffic.
Yes, because like or not that’s the only possible solution. If all traffic was required to be signed and the signatures were tied to an entity then you could refuse unsigned traffic and if signed traffic was causing problems you’d know who it was and have recourse.
I don’t like this solution but it’s the only way forward that I can see.
How do you have more recourse countering a random third world IP vs a random third world person when both are outside your juridiction?
Unsigned traffic = drop. Signed traffic that becomes an annoyance = drop. If signed traffic becomes more than an annoyance then you know who to report to the authorities and even in Brazil there’s authorities.
deleted by creator
PoW has the advantage of being anonymous but I don’t like it as solution for the simple fact that it uses more electricity. It’s just not a very green solution.
deleted by creator
Yep, it hit many lemmy servers as well, including mine. I had to block multiple alibaba subnet to get things back to normal. But I’m expecting the next spam wave.
The Linux Mint forums have been knocked offline multiple times over the last few months, to the point where the admins had to block all Chinese and Brazilian IPs for a while.
This is the first I’ve heard about Brazil in this type of cyber attack. Is it re-routed traffic going there or are there a large number of Brazilian bot farms now?
I don’t know why/how, just know that the admins saw the servers were being overwhelmed by traffic from Brazilian IPs and blocked it for a while.
I too read Drew DeVault’s article the other day and I’m still wondering how the hell these companies have access to “tens of thousands” of unique IP addresses. Seriously, how the hell do they have access to so many IP addresses that SysAdmins are resorting to banning entire countries to make it stop?
If you get something like 156.67.234.6, then 7, then 56 etc just block 156.67.0.0/24
Sure, network blocking like this has been a thing for decades but it still requires ongoing manual intervention which is what these SysAdmins are complaining about.
There are residential IP providers that provide services to scrapers, etc. that involves them having thousands of IPs available from the same IP ranges as real users. They route traffic through these IPs via malware, hacked routers, “free” VPN clients, etc. If you block the IP range for one of these addresses you’ll also block real users.
There are residential IP providers that provide services to scrapers, etc. that involves them having thousands of IPs available from the same IP ranges as real users.
Now that makes sense. I hadn’t considered rogue ISPs.
It’s not even necessarily the ISPs that are doing it. In many cases they don’t like this because their users start getting blocked on websites; it’s bad actors piggy-packing on legitimate users connections without those users’ knowledge.
deleted by creator
fail2ban
I’m familiar with f2b. I even have several clients licensed with the commercial version but it doesn’t fit this use case as there’s no logon failure for it to work with.
I automatically ban any IP that comes from outside the US because there’s literally no reason for anyone outside the US to make requests to my infra.
I have systems setup with geo-blocking but it’s of limited use due to the prevalence of VPNs.
also, use a WAF on a NAT to expose your apps.
This isn’t a solution either because a WAF has no way to know what traffic is bad so it doesn’t know what to block.
Removed by mod
nepenthe
It’s a Markov-chain-based text generator which could be difficult for people to implement on repos depending upon how they’re hosting them. Regardless, any sensibly-built crawler will have rate limits. This means that although Nepenthe is an interesting thought exercise, it’s only going to do anything to things knocked together by people who haven’t thought about it, not the Big Big companies with the real resources who are likely having the biggest impact.
Removed by mod
any way of slowing things down or wasting resources is a gain I guess
AI scrapping is so cancerous. I host a public RedLib instance (redlib.nadeko.net) and due to BingBot and Amazon bots, my instance was always rate limited because the amount of requests they do is insane. What makes me more angry, is that this fucking fuck fuckers use free, privacy respecting services to be able to access Reddit and scrape . THEY CAN’T BE SO GREEDY. Hopefully, blocking their user-agent works fine ;)
Thanks for hosting your instances. I use them often and they’re really well maintained
I posted on your guestbook but the link was broken.
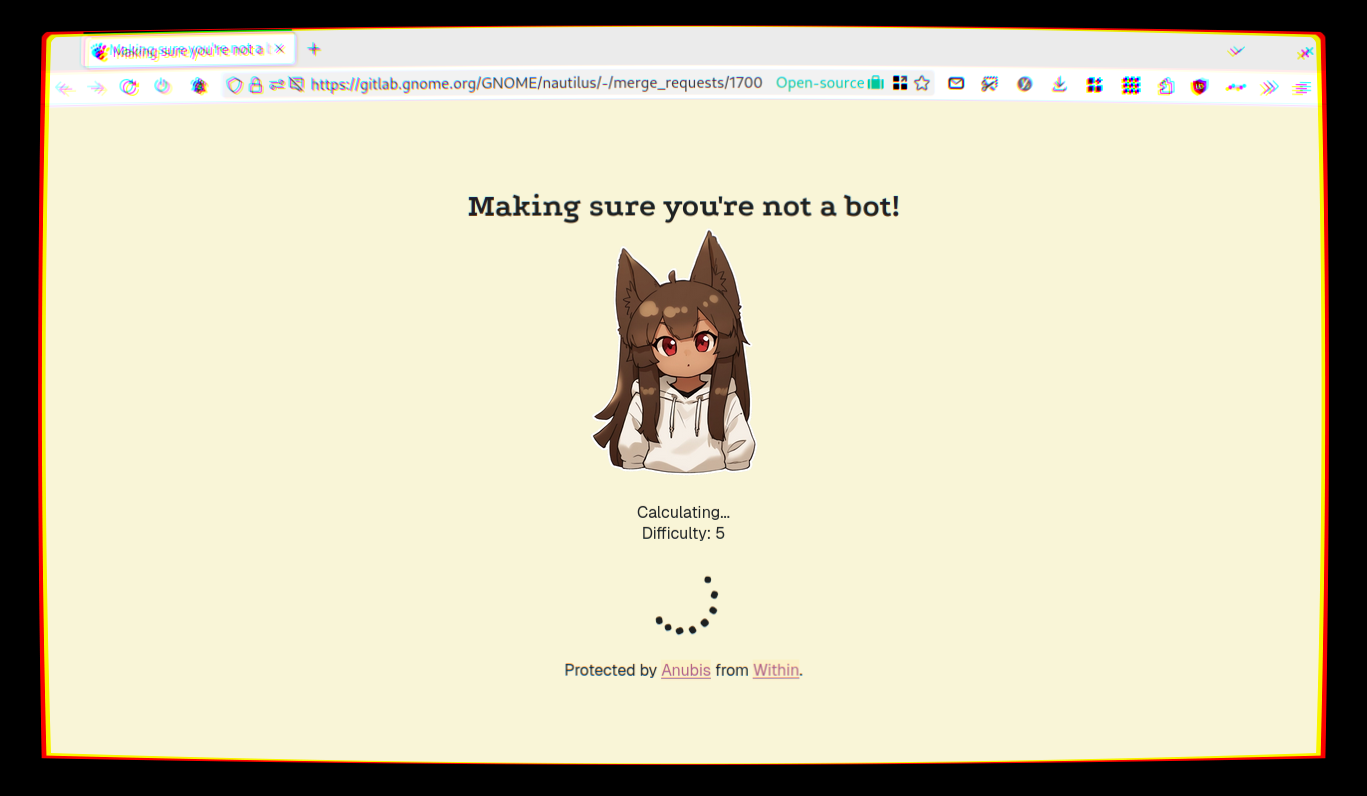
I’d say be wary of Anubis author.
I noticed you started using Anubis recently. Take a look here https://github.com/Xe/x/issues/701 also PRs 702, 703, 704
-She made GNOME say something the project doesn’t agree
-She tried to push her beliefs where it was unnecessary and disrespectful
-She still refuses to remove things in her code that is disrespectful, some are mere comments and serves no real purpose
-She refused to accept PRs, discuss changes, refuse dictionary definitions seemingly because of her ego
-After all that she locked conversations in the issue/PRs as a result nobody else can show support nowIf she has a belief, there are other mediums/ways to express it, why like this?
This is unwelcoming and definitely not FOSS spirit.
ELI5 why the AI companies can’t just clone the git repos and do all the slicing and dicing (running
git blameetc.) locally instead of running expensive queries on the projects’ servers?Because that would cost you money, so just “abusing” someone else’s infrastructure is much cheaper.
Takes more effort and results in a static snapshot without being able to track the evolution of the project. (disclaimer: I don’t work with ai, but I’d bet this is the reason and also I don’t intend to defend those scraping twatwaffles in any way, but to offer a possible explanation)
Also having your victim host the costs is an added benefit
Too many people overestimate the actual capabilities of these companies.
I really do not like saying this because it lacks a lot of nuance, but 90% of programmers are not skilled in their profession. This is not to say they are stupid (though they likely are, see cat-v/harmful) but they do not care about efficiency nor gracefulness - as long as the job gets done.
You assume they are using source control (which is unironically unlikely), you assume they know that they can run a server locally (which I pray they do), and you assume their deadlines allow them to think about actual solutions to problems (which they probably don’t)
Yes, they get paid a lot of money. But this does not say much about skill in an age of apathy and lawlessness
Also, everyone’s solution to a problem is stupid if they’re only given 5 minutes to work on it.
Combine that with it being “free” for them to query the website and expensive to have enough local storage to replicate, even temporarily, all the stuff they want to scrape and it’s kind of a no brainier to ‘just not do that’. The only thing stopping them is morals / whether they want to keep paying rent.
deleted by creator
If an AI is detecting bugs, the least it could do is file a pull request, these things are supposed to be master coders right? 🙃
to me, ai is a bit like bucket of water if you replace the water with “information”. Its a tool and it cant do anything on its own, you could make a program and instruct it to do something but it would work just as chaotically as when you generate stuff with ai. It annoys me so much to see so many(people in general) think that what they call ai is in anyway capable of independent action. It just does what you tell it to do and it does it based on how it has been trained, which is also why relying on ai trained by someone you shouldnt trust is bad idea.
It’s also a huge problem for library/archive/museum websites. We try so hard to make data available to everyone, then some rude bots come along and bring the site down. Adding more resources just uses more resources–the bots expand to fill the container.
Assuming we could build a new internet from the ground up, what would be the solution? IPFS for load-balancing?
deleted by creator
Maybe letters through the mail to receive posts.
so basically what you are saying is to not put information on public places, but only send information to specific people
deleted by creator
How long will USPS last?
what would be the solution?
Simple, not allowing anonymous activity. If everything was required to be crypto-graphically signed in such a way that it was tied to a known entity then this could be directly addressed. It’s essentially the same problem that e-mail has with SPAM and not allowing anonymous traffic would mostly solve that problem as well.
Of course many internet users would (rightfully) fight that solution tooth and nail.
Proof of work before connections are established. The Tor network implemented this in August of 2023 and it has helped a ton.
PoW uses a lot of electricity on the client side so environmentally it’s a poor solution, especially at scale.
For just accessing a simple resource, it does not use a whole lot of power because it only gets activated when the resource is under load and it helps to sort traffic based on effort placed to the POW puzzle. You can choose to place zero effort and be put in the back of the line, but people who choose to put in some small effort will be put in front of you, and people who put in a larger effort will be in front of them until the resource is no longer oversubscribed, and then it will drop back down to zero. That’s how the Tor network handles it and it works incredibly well. It has stopped the denial of service attacks in their tracks. In most cases, it’s hardly ever even active. Just because it is there, deters attacking it.
No, that’s not a solution, since it would make privacy impossible and bad actors would still find ways around.
Removed by mod
AI will come up there to abuse it as well
They’re afraid
Failtoban should add all those scraper IPs, and we need to just flat out block them. Or send them to those mazes. Or redirect them to themselves lol
I’m not sure how they actually implemented it, but you can easily block ML crawlers via cloud flare. Isn’t just about every small site/service behind CF anyway?
Last I checked, cloudflare requires the user to have JavaScript and cookies enabled. My institution doesn’t want to require those because it would likely impact legitimate users as well as bots.
Huh? I can reach my site via curl that has neither. How did you come up with this random set of requirements?
Odd. I just tried
and got
Enable JavaScript and cookies to continue
I’m clearly not on the same setup as you are, but my off-the-cuff guess is that your curl command was issued from a system that cloudflare already recognized (IP whitelist, cookies, I dunno).
Anyways, I’m reading through this blog post on using cURL with cloudflare-protected sites and I’m finding it interesting.
Of course their challenge requires those things. How else could they implement it? Most users will never be presented with a challenge though and it is trivial to disable if you don’t want to ever challenge anyone. I was just saying CF blocks ML crawlers.